Fritz!Box 7530 – How to Close Port 8089 and Disable TR-069
A security guide to disabling the TR-069 protocol and closing the open port 8089 on your Fritz!Box 7530 router for better network security.
A few months ago, VDSL finally arrived at my home – with all the typical Italian timing. What better excuse to buy a new DSL router? My previous ASUS unit hadn’t been updated in years and was surviving on questionable community-developed beta firmware.
I hadn’t shopped for a home VDSL router in ages. The choices were overwhelming, but the Fritz!Box reviews stood out with impressive performance and stability metrics. Long story short: I got a beautiful Fritz!Box 7530 – which is actually aesthetically pleasing, unlike the more… Teutonic alternative versions.
I can confirm it’s excellent – works well and does its job reliably. The web interface is comprehensive, though not exhaustive: some power-user features might be missing, but overall it’s hard to complain.
Let’s get to the point.
The Security Audit
I had previously tweaked the router to:
- Optimize VDSL settings
- Disable all unnecessary “services” (there are many):
- AVM Services: automatic firmware checks, MyFritz, etc.
- Firewall settings: NetBIOS (lol), stealth mode, etc.
After several months, I decided to run an external security audit: let’s run nmap from outside and see what’s exposed.
The result was… concerning.
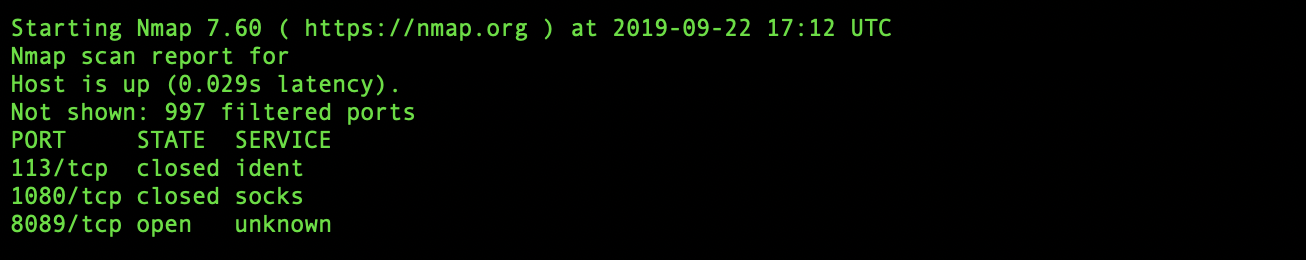
$ nmap -Pn host
Starting Nmap 7.60 ( https://nmap.org ) at 2019-09-22 17:12 UTC
Nmap scan report for host
Host is up (0.029s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
113/tcp closed ident
1080/tcp closed socks
8089/tcp open unknownGood news: stealth mode is working – the only way to successfully run nmap is to skip the host online check (-Pn).
Bad news: port 8089 is OPEN.
What is Port 8089?
A quick search revealed the culprit: Internet Security Diagnostics: TR-069
What does this service do?
TR-069 (Technical Report 069) is a protocol for data exchange between a service provider’s server and a customer’s terminal device.
TR-069 is frequently used by broadband providers for remote configuration of DSL routers.
TR-069 performs the following tasks:
- Automatic configuration and dynamic service activation
- Firmware management
- Status and performance monitoring
- Remote diagnostics and maintenance
The obvious question: what if I don’t want my ISP to remotely configure my router?
The answer is frustrating: you can’t disable it from the interface. The official documentation simply “reassures” us about security.
Dear AVM: an open port is always an open port.
The Solution
Let me save you the headache and explain how to disable TR-069.
Step 1: Install FBEditor
Download any version of FBEditor from GitHub.
FBEditor is a simple tool that downloads the textual configuration from Fritz!Box routers. Unfortunately, it’s only available as EXE or JAR – use Java if needed.
Step 2: Retrieve the Configuration
Connect to your router and download the current configuration.
Step 3: Disable TR-069
Find tr069cfg and set it to disabled:
tr069cfg {
# enabled = yes;
enabled = no;
}This should be sufficient, but I also made these additional changes:
-
Comment out the forward rules:
# tr069_forwardrules = "tcp 0.0.0.0:8089 0.0.0.0:8089"; -
Disable TR-069 discovery:
tr069discover_active = no;
Step 4: Apply the Configuration
Upload the modified configuration. The router will perform a quick reboot.
Result
After these changes, port 8089 is closed and your router is no longer listening for ISP remote management commands. Your network is more secure. 🔒
Have questions about router security or network configuration? Feel free to reach out!